
Scrambling for audit evidence a week before an assessment is passé. In 2025, we bake compliance checks into everyday workflows so you catch—and fix—drift before anyone notices. That always-ready stance is called continuous (always-on) compliance monitoring: software that connects to your cloud, laptops, identity provider, and code repos, gathers proof automatically, and flags issues in real time. With the Department of Defense’s CMMC rule taking effect on November 10, 2025, year-round vigilance isn’t optional. This guide compares seven leading platforms that keep you audit-ready and helps you choose the best fit.
Why continuous beats periodic audits in 2025
Annual audits worked when infrastructure changed monthly. Now, cloud instances spin up in minutes and regulations shift just as quickly. A once-a-year snapshot cannot keep pace with that motion.
Regulators have made the point clear. Under the Department of Defense’s final CMMC rule, effective November 10, 2025, defense contractors must sign an annual affirmation of continuous compliance and report any lapse right away, not just during a triennial assessment.
Business complexity adds more pressure. One SaaS provider may pursue SOC 2 for U.S. customers, ISO 27001 for the EU, and HIPAA for health data. Because multifactor authentication maps to all three, a platform that cross-walks controls turns a single fix into three green checks.
Tooling has caught up. According to Vanta, the platform streams real-time telemetry through hundreds of connectors and lists more than 375 native integrations. Each control is tested on a rolling schedule. When drift appears, the software pings Slack or opens a Jira ticket so your team can repair issues long before an auditor arrives.
Spreadsheets cannot compete. Manual evidence collection often misses weeks of misconfigurations, which triggers a last-minute scramble that still leaves gaps. Continuous monitoring surfaces problems the day they happen, lets you remediate fast, and keeps the scorecard green between audits—not just on audit day.
How to evaluate continuous compliance tools
Choosing software is easier once you know what “good” looks like. We rely on seven yardsticks, beginning with the foundation: integrations.
1. Integrations: breadth and depth
A platform lives or dies by the evidence it can see. Prioritize tools that connect to your cloud, identity provider, code repo, laptops, and ticketing system within minutes. Vanta, for instance, lists more than 375 native integrations (from AWS to Jamf), which removes the need for screenshots and lets future SaaS additions appear automatically.
2. Framework coverage and control mapping
Once data is flowing, the real test is how many rulebooks the platform can translate that evidence into. Leading tools ship with large libraries: Hyperproof lists 118 framework templates out of the box, while Vanta supports all three CMMC levels plus 35 other standards. They also tag each control so one action, such as enforcing multifactor authentication, satisfies SOC 2, ISO 27001, HIPAA, and CMMC at the same time. This cross-mapping turns a stack of checklists into one cohesive plan and removes duplicate work when a new certification lands on your roadmap.
3. Automated evidence collection and testing
Evidence ages fast, which is why the most effective platforms interrogate systems on a rolling schedule rather than waiting for a quarterly check. According to Vanta, many core cloud-security tests run every hour, which means something as small as spinning up a new server triggers an immediate check of its encryption settings. The result is logged with a timestamp and added directly to the audit trail.
This type of machine-verified feed replaces hours of screenshot hunting and ensures you learn about failing controls the same day they appear. By automating evidence collection at that cadence, teams remediate issues before auditors or customers ever see a gap, keeping the scorecard green continuously instead of only at audit time.
4. Alerting and remediation workflow
Spotting an issue is only half the job; closing it keeps auditors happy. Modern platforms create a task as soon as a control fails, then push it into your workflow tool of choice. Hyperproof, for example, offers bidirectional Jira sync, so comments, status changes, and attachments travel both ways. Your engineer sees the ticket in Jira, fixes the misconfigured S3 bucket, and Hyperproof flips the control back to “pass” automatically.
Fast feedback loops matter. When remediation tasks live where developers already work, fix ships sooner and nothing slips through the cracks. Executives see a live dashboard of outstanding compliance debt and can free resources before a minor gap grows into an audit-day crisis.
5. Reporting and auditor-ready exports
On audit day, clarity beats volume. Robust platforms gather every log, policy, and screenshot in one click and, critically, invite the auditor into a read-only portal. Vanta’s Auditor View lets assessors browse evidence without email back-and-forth, while you control what they can see or download.
That self-service hand-off shrinks review cycles from days to hours. Instead of hunting for files, you answer the few strategic questions an assessor still needs to ask, proving that your environment is monitored continuously, not cobbled together at the last minute.
6. User permissions and audit trails
Compliance data is sensitive, so access controls must be as granular as the controls they guard. Look for role-based permissions that let:
Auditors browse evidence in read-only mode
Engineers upload or edit proof only for the systems they own
Executives view high-level metrics without swimming in detail
Hyperproof, for instance, offers Manager, Contributor, and Viewer roles inside each audit, plus a dedicated External Auditor role limited to the audits you select.
Equally vital is an immutable audit trail. Every action (who uploaded a file, who marked a test as passed, who closed a ticket) should be stamped with user, time, and reason. Hyperproof’s audit-log feature captures that metadata automatically and protects it from edits, giving you a defensible chain of custody. Auditors get the transparency they expect, and your incident reviewers see exactly how decisions were made.
7. Time-to-value and ease of onboarding
A platform pays off only when real data starts flowing. The best tools move you from first login to live monitoring in days, not quarters. Vanta reports that customers who automate SOC 2 cut the process from six to twelve months down to about three to six months—roughly half the time of manual prep.
Speed also buys breathing room. If a contract requires CMMC evidence in six months, hitting “green” status in the first few weeks lets you focus on deeper remediation later. During evaluations, ask vendors for customer timelines: How long did a peer company your size take to reach audit readiness? Verified numbers turn a glossy demo into a concrete delivery date.
Look for accelerators such as setup wizards, CSV import of HR data, and libraries of pre-written policies; each can save hours or even weeks.
Top 6 Continuous Compliance Platforms for 2025
Use this section to shortlist 2–3 candidates aligned to your environment and deadlines—especially if you’re targeting CMMC readiness by November 10, 2025.
Vanta: automation-first CMMC compliance

Vanta is built for “always-on” audit readiness. It lines up every CMMC practice across Levels 1–3 in a guided checklist, auto-maps overlaps to NIST 800-171/172, and pulls live evidence from 375+ native integrations (AWS, Azure/GCP, Okta/Azure AD, GitHub/GitLab, Jamf/Intune, HRIS, and more). Its CMMC compliance software helps teams get ready for certification and stay compliant over time by pairing automated testing with prescriptive guidance across controls and documents. A lightweight Device Monitor covers endpoints (disk encryption, screen lock, OS patching), so controls tied to laptops and desktops get verified continuously, not once a year. When a control drifts, Vanta raises an alert and can open a Jira/ServiceNow task with ownership and due dates; once the fix lands, the failing test flips to green and your CMMC dashboard updates in real time.
Beyond collection, Vanta smooths the auditor handoff. You can invite assessors into a read-only Auditor Portal or one-click export evidence bundles by control family, cutting the email back-and-forth that slows assessments. If you’re already on SOC 2 or ISO 27001, Vanta’s cross-framework mapping reuses existing controls to accelerate your CMMC track, which is especially helpful for contractors working toward the DoD CMMC milestone on November 10, 2025. A curated network of RPO/C3PAO partners plus a sandbox/demo environment round out the experience, letting teams trial workflows before wiring up production.
Trade-offs: Pricing is sales-assisted (no public tiers), and Vanta doesn’t auto-generate SSP/POA&M or handle eMASS submissions in-product—you’ll use partners or internal processes while tracking tasks in Vanta.
Scrut Automation: unified compliance for fast-growing teams
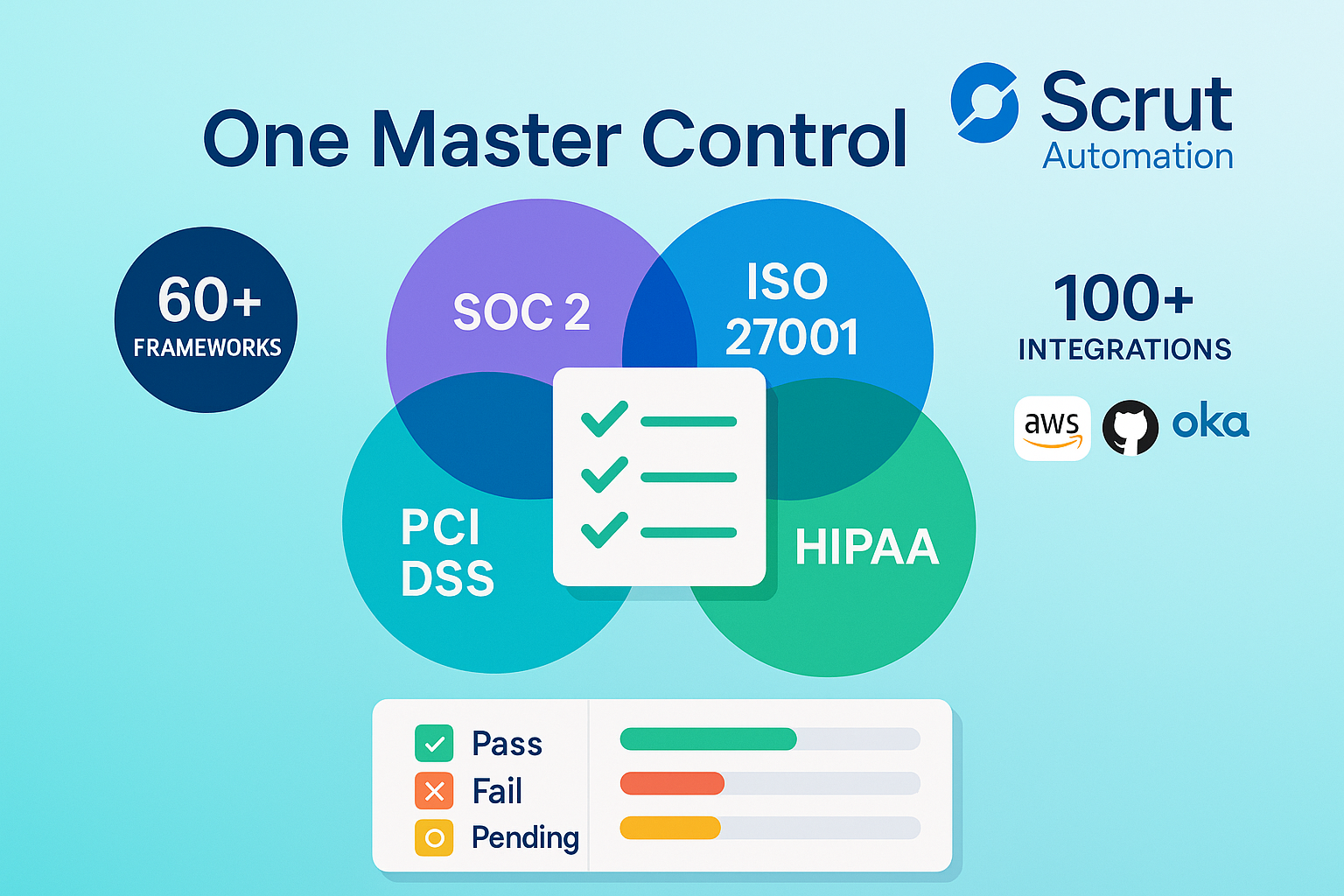
Scrut blends the power of a GRC suite with the simplicity of a checklist app. Select the frameworks you need—SOC 2, ISO 27001, PCI DSS, HIPAA, or any of the more than 60 out-of-the-box standards Scrut supports. The platform builds one master control set, showing exactly where requirements overlap.
Setup is developer-friendly: OAuth into AWS, GitHub, Okta, and your HR system, then watch Scrut’s over 100 integrations start populating evidence automatically. A clean dashboard scores each control—pass, fail, or pending—so misconfigured buckets surface before the weekly security meeting.
Breadth does not equal bloat. Scrut layers in a vendor-risk module, more than 200 policy templates, and a public Trust Center, yet the interface stays approachable for teams without a dedicated compliance officer. If you are climbing from a first SOC 2 audit to a multi-cert program, Scrut lets you manage the ascent without juggling multiple tools.
Hyperproof: multi-framework powerhouse
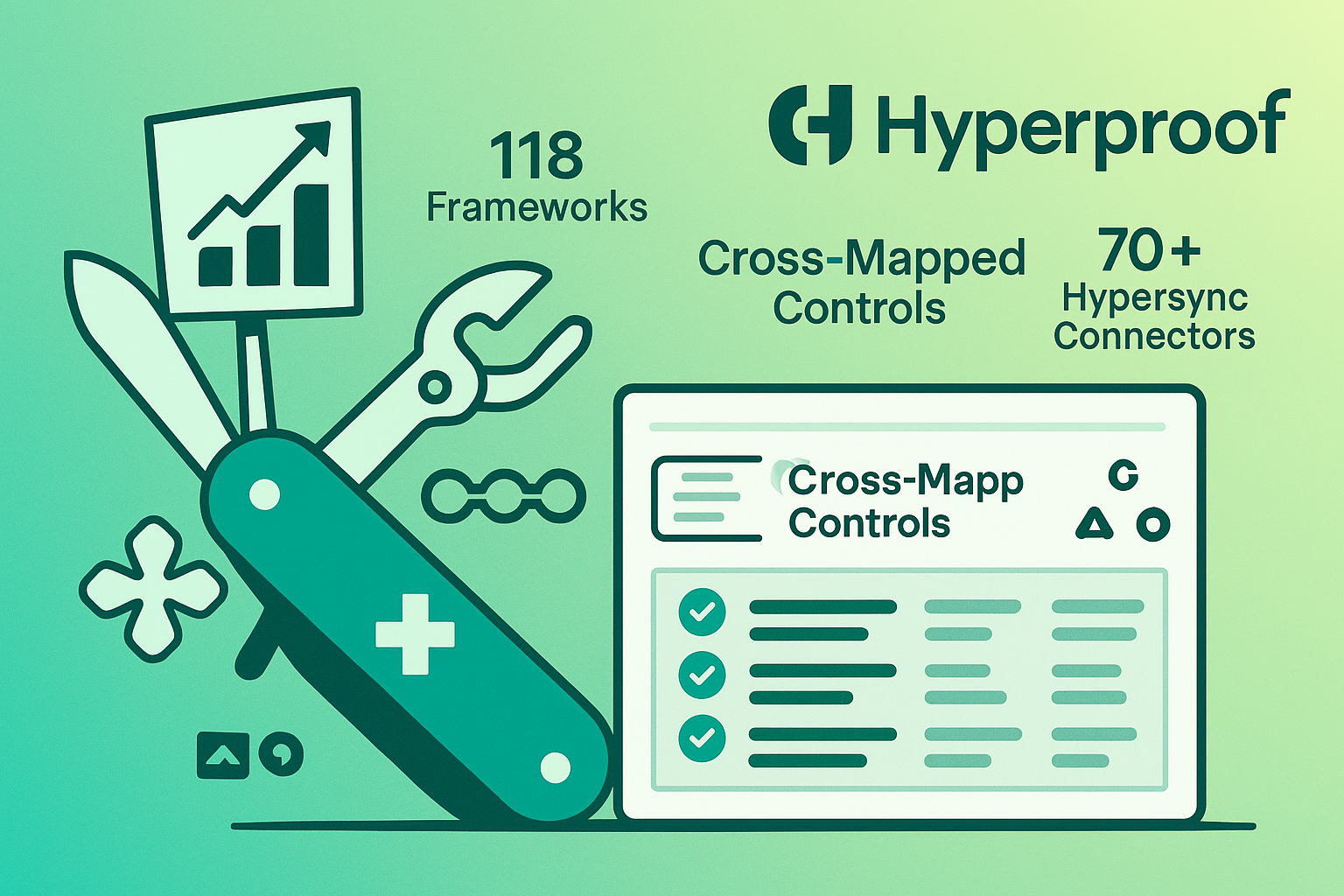
Hyperproof is the Swiss Army knife of this roundup. It ships with 118 framework templates and cross-maps them automatically, so a single access-control fix satisfies SOC 2, ISO 27001, GDPR, and whatever acronym regulators add next quarter.
Its more than 70 Hypersync connectors pull fresh evidence on the cadence you set. When drift appears, Hyperproof opens a Jira, ServiceNow, or Asana task so the right owner gets nudged inside their everyday workflow.
Scope management is the sleeper feature. If your company spans multiple product lines or subsidiaries, you can partition controls and evidence per entity yet still roll everything up for a board-level view—ideal for midsize firms moving from a first audit into a full GRC program.
RegScale: DevOps-inspired compliance as code

RegScale treats compliance like infrastructure: you write it, version it, and test it in the pipeline. Built on NIST OSCAL, the platform hooks into CI servers, Terraform plans, and cloud APIs, then runs automated control checks on every build. If encryption settings or IAM policies drift, the build fails before non-compliant resources reach production.
That shift-left model resonates with engineering-led teams and defense contractors that need real-time CMMC or FedRAMP assurance without slowing release cycles. RegScale reports that customers achieve FedRAMP High three to four times faster than with legacy GRC tools, at roughly 50 percent of the traditional cost.
The platform also auto-generates living documentation—a System Security Plan that updates itself after every commit—so auditors see facts that match the current environment, not last quarter’s screenshots.
The trade-off is culture: teams must embrace “compliance as code” for RegScale to shine. When they do, manual paperwork shrinks, and compliance status moves as quickly as the release cadence.
Apptega: streamlined compliance for lean teams
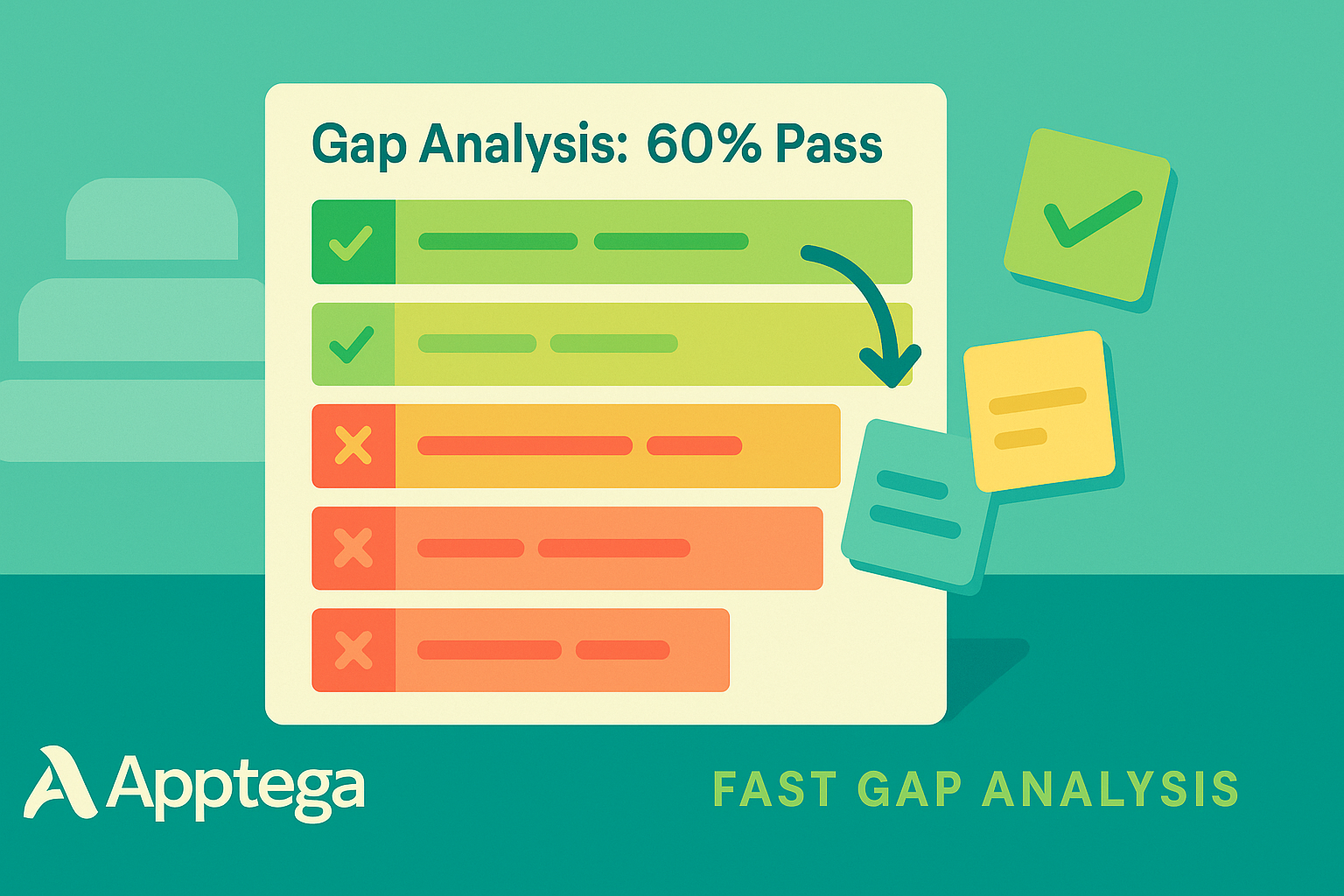
Apptega trades deep automation for approachability. A startup can sign up, choose from more than 30 framework templates (including SOC 2, NIST CSF, and CMMC Level 1), and see a color-coded gap analysis within hours. Drag-and-drop tasks, policy builders, and a Starter plan with a 14-day free trial lower the barrier further, so founders without a security hire can still track the basics.
Integrations are modest—about 25 connectors for widely used tools such as Microsoft 365 and Qualys—but Apptega compensates with reminders and checklists that make manual steps explicit. Managed service providers also like its multi-tenant view, which lets one consultant track dozens of client programs from a single dashboard. For teams that need structure more than sophisticated telemetry, it is the quickest path off spreadsheets.
CyberSaint: risk-driven continuous compliance

CyberSaint starts with a board-level question: “How much cyber-risk did we reduce this quarter?” Its CyberStrong platform answers by pairing continuous control data with dollar-based risk figures, so every compliance fix moves the metric executives care about.
A patented AI engine, recognized in the 2025 Gartner Hype Cycle for Cyber-Risk Management under Continuous Controls Monitoring and AI in GRC categories, sifts vulnerability scans, asset inventories, and ticket systems to grade each control beyond pass or fail. Dashboards translate those insights into business language while still letting analysts drill into raw evidence.
The catch is complexity. Deploying CyberSaint feels more like launching a program than installing an app. Enterprises with dedicated GRC staff gain the most, using features such as Continuous Controls Automation to cut assessment effort by up to 90 percent. For Fortune-scale organizations juggling SOX, CMMC, and sector-specific regulations, tying compliance work directly to quantified risk can justify the investment.
Mini walk-through: continuous compliance in action
Picture a fast-growing SaaS company that just connected a monitoring platform. Here is how your first week can look.
Day 1: Connect systems. An admin OAuths AWS, GitHub, Okta, and the laptop-management tool. Within minutes the platform inventories buckets, repos, user lists, and device settings, using only API keys and OAuth screens.
Day 2: Auto-map controls. The software maps those feeds to CMMC Level 2. All 110 practices light up green, yellow, or red; the dashboard shows 60 passes, 40 gaps, and 10 items awaiting confirmation.
Day 3: Spin up continuous tests. Core checks now run hourly—a cadence Vanta recommends for high-value controls. If a developer forgets MFA on a service account, the platform flags the drift, posts a Jira ticket, and pings Slack. The engineer enables MFA, and the control flips back to green on the next check.
Day 5: Review progress. Executives open a real-time scorecard reading 88 percent compliant, up from 55 percent on Monday. They assign the remaining reds and set due dates. An invited auditor browses the read-only portal and verifies dozens of controls without an email chain.
From integration to live risk reduction, the cycle takes days, not months, turning compliance from a fire drill into a steady heartbeat.
ROI and time-to-value
Continuous monitoring requires investment, yet data shows you get it back quickly.
Time saved. IDC reports that companies using Vanta spend 82 percent less time per audit because evidence collection is automated. Hyperproof customers see a 50 percent drop in audit-response hours after centralizing requests on the platform.
Cost avoided. Catching drift the day it occurs turns a simple Jira ticket into the fix, instead of an emergency overhaul that can cost five figures. One Vanta Seamless Audit case study shows an 80 percent reduction in total audit completion time, eliminating rush surcharges and extra billable hours.
Faster revenue. An always-green dashboard shortens security reviews. Vanta customers complete five times more customer reviews within a week after launching a Trust Center, helping deals close sooner.
Combine those gains and most firms recover the subscription within the first audit cycle, often in less than twelve months, while freeing your team to focus on higher-value security work.
Buying checklist and decision rules
Use this five-step gut check before you sign a contract.
Verify framework coverage. Need CMMC Level 2 next year? Skip any vendor without native NIST 800-171 mapping; retro-fitting later costs more than switching now.
Match your tech stack. List every cloud account, identity provider, code repo, and endpoint manager. Choose a platform that covers at least 90 percent of that list out of the box. Each missing connector adds manual work you never get back.
Gauge team bandwidth. Developer-centric tools such as RegScale excel when engineers own “compliance as code,” but they can swamp a two-person IT shop. Template-first tools like Apptega suit lean teams yet can feel restrictive for large enterprises with custom risk models.
Check export options. If auditors want PDFs, be sure the platform bundles evidence with one click. If they prefer portals, invite them to a read-only demo and track their feedback; the reaction tells you more than a brochure ever will.
Demand time-to-value proof. Ask each vendor for a customer story your size and confirm how long it took to reach audit readiness. Hyperproof reports clients who cut SOC 2 prep by 50 percent in three months, while Vanta shows an 82 percent reduction in audit hours for similar firms. If timelines feel vague, keep shopping.
These five checks separate shiny demos from platforms that deliver, saving you from buyer’s remorse later. If you want to see how those five checks translate into real-world reporting, this step-by-step risk-register dashboard guide walks through turning raw control data into heat-maps, owner charts, and audit-ready exports.
FAQs
Do I need continuous monitoring to pass CMMC? Strictly speaking, CMMC doesn’t mandate a specific tool—but Level 2 expects you to maintain controls year-round, not just at audit time. Continuous monitoring is the practical way to prove that ongoing posture, catch drift fast, and document remediation.
How many integrations are “enough”? List your core systems (cloud, IdP, code repo, device management, ticketing, HRIS). If a platform natively covers ~90%+ of that list, you’re in good shape. Every missing connector becomes recurring manual work.
What evidence do auditors actually want from these tools? Objective, timestamped proof mapped to controls: config states (e.g., MFA on), access logs, device posture, policy acknowledgments, and a clear audit trail of who fixed what, when. Bonus if you can grant read-only portal access instead of emailing ZIPs.
How long does implementation usually take? For a focused team, connecting core systems and turning on baseline tests is often days to a couple of weeks; reaching audit-ready depends on your gaps (typically weeks to a few months). Ask vendors for peer timelines and a pilot plan.
What’s the biggest hidden cost buyers miss? Underestimating manual effort for non-integrated systems and onboarding time. Budget hours for policy tuning, role/permission setup, and ticket workflows—and confirm in advance how you’ll handle any systems without native connectors.
Conclusion: pick, pilot, and lock in year-round readiness
Continuous compliance only pays off when it’s woven into daily work. With CMMC enforcement landing on November 10, 2025, the winning move is to narrow your list to 2–3 platforms, validate integrations against your stack, and run a time-boxed pilot that proves three things: (1) automated evidence really replaces screenshots, (2) alerts flow into your team’s workflow (Jira/ServiceNow/Slack) and get closed on SLA, and (3) auditor handoff is low-friction.
Use the evaluation yardsticks above to score each tool, then choose the option that hits framework coverage, integration depth, and onboarding speed for your environment. Stand up continuous tests early, set owner-based remediation rules, and schedule a dry-run evidence export with your assessor. Do that, and compliance shifts from scramble to steady state—keeping you audit-ready in 2025 and beyond.

